The healthcare industry is a lucrative area for software development companies. There is a wide range of needs from doctors and patients that can be solved with appropriate computer programs. However, the regulations in this field are very strict. Since 1996, the United States government has been protecting patients’ privacy with the Health Insurance Portability and Accountability Act (HIPAA). The Act covers multiple aspects: from hospital operations to staff actions, and has certain obligatory requirements for digital technologies. Let’s discover how to make your software HIPAA-compliant.
Two general cases when your software needs HIPAA compliance
Software that seeks HIPAA compliance usually comes from two different sources. This means that development companies that offer the services of ensuring HIPAA compliance have two target types of clients.
1. A client already has a working computer program and wants to adapt it to the USA market.
There are several variants of this scenario. A client may own a healthcare-related software that operates outside the United States. As a part of its expansion strategy, they want to try the American market, but they need to follow the HIPAA guidelines, which means changing the software application. For example, a telemedicine application that is employed effectively in Europe must achieve HIPAA compliance in order to be used in the United States.
Alternatively, a client may have a software solution unrelated to medicine, but they want to extend its functionality and cover this industry. This is a rather common case for various ERP and CRM systems, messengers, video conference apps, etc.
A well-known illustrative example of such a case is Zoom. The popular messaging app that gained global recognition and millions of fans has paid Healthcare plans that are HIPAA-compliant and start from $200 per month. So, such compliance is not only a necessity but also an effective way of monetization. This example shows that the additional costs of ensuring HIPAA compliance can be easily recovered. Most people understand the importance of protecting confidential information at the highest level and are willing to pay for improved data security even when the application itself is free.
2. A client has an idea or a startup targeted at the healthcare software market in the USA
If a client comes with a fresh idea for a medical app, from a small hormone dosage calculator to a comprehensive hospital management system, they should realize how important HIPAA compliance is. And significant fines for intentional or unintentional data breaches are an excellent proof and a reminder of this importance.
The Department of Health and Human Services and its Office for Civil Rights (OCR), in particular, have issued 11 penalties for violating HIPAA rules in 2018. While 11 penalties may sound insignificant as a number, they led to over $28 million worth of fines, the average fine being about $2.6 million. Moreover, as of the second half of 2020, the total amount of penalty cases is 77, and the sum of fines has reached $117,368,582! So, if you are not ready to dish out several million dollars while being kicked out of the market with a bad reputation, ensure that your software is HIPAA-compliant.
Reasons and subjects of HIPAA
The United States authorities devised and implemented HIPAA in order to add some needed norms and guidelines for handling protected health information (PHI). Recently, due to the digital transformation in the field of health care, the term “electronic protected health information” (ePHI) was also introduced to this Act.
These two types of confidential information are highly sensitive due to its tremendous potential impact if patient data falls into the wrong hands. Such data breaches can result in financial and reputational losses or may be used for blackmail or money extortion.
(E)PHI comprises several specific categories of personal information or information that can be correlated with other data to reveal the identity of a patient. Therefore, (electronic) protected health information includes, among others:
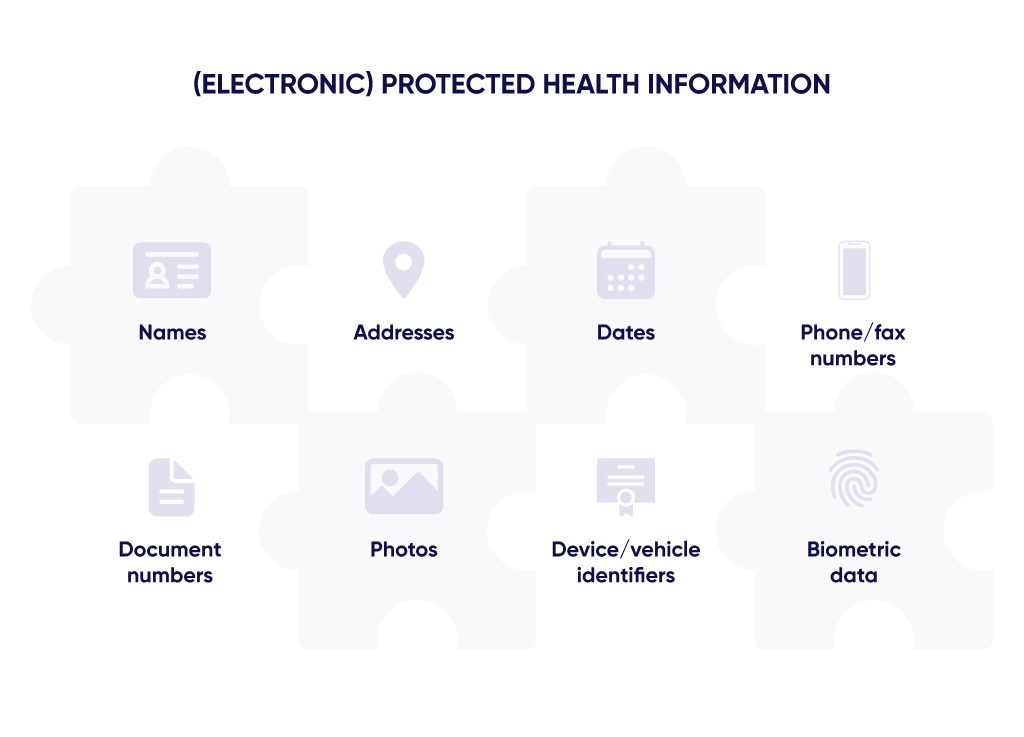
- Names of patients as well as names of the medical staff that are involved in their treatment.
- Most types of addresses, including physical and e-mail addresses of patients, as well as zip codes. Additionally, IP (Internet Protocol) addresses are also covered by HIPAA.
- Most dates related to patients and their interactions with healthcare institutions. For example, date of birth/death, dates of doctor visits, admission to or discharge from a hospital, and so on.
- Phone numbers. Fax numbers are also included, despite the fact that you can barely find a working fax machine these days.
- Document-related numbers including those of social security, insurance cards, medical records, bank accounts, licences or certificates, and much more. Generally, if a personal document has a number, it is protected by HIPAA.
- Photographic images, even if the face of a patient is not seen in the picture. Generally, all medical photos of any body part belong to this category.
- Numbers or other identifiers of devices and vehicles. This category includes serial numbers, license plate numbers, and so on.
- Biometric data that allows personal identification. Fingerprints, retina scans, and voiceprints are among the most common means of authorization in smart devices that can give access to PHI. That’s why they are also considered protected health information. Any voice recordings, regardless of the contents, are also protected by HIPAA.
This list is not exclusive, but it provides a general understanding of data that must be protected according to HIPAA requirements. More provisions were added over the years to the original Act in order to cover more scenarios and adapt it to the progress of digital technologies. Thus, the HIPAA Privacy Rule that had set up the base protection for medical records got amendments and additions in the form of the Security Rule in 2005 and the Omnibus Rule in 2013.
There is also a Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009 that focuses on electronic health records and complements HIPAA in many ways. Considering this trend, we will definitely see further updates to the above-mentioned rules and acts in the future.
In order to achieve respective compliance, a software solution must provide means to ensure such protection. The HIPAA regulations apply to hospitals and other healthcare providers that are regarded as Covered Entities in legal terms, as well as all kinds of personnel who have access to PHI and are considered Business Associates. As this software is intended for use in healthcare organizations and institutions by medical staff and is involved in the collection, transmission, storage, or use of the (e)PHI, the rules of the Act also apply to it.
HIPAA Compliance Checklist
The most common and illustrative way of implementing HIPAA compliance into software development is via a checklist. When developers integrate the means for ensuring a particular HIPAA requirement, you can mark it as fulfilled and proceed to another one.
The Security Rule comprises three types of required or addressable safeguards. The Administrative and Physical Safeguards are more focused on action protocols for Covered Entities and Business Associates, device use policies, physical access control, and other aspects that are rather distant from software development.
The Technical Safeguards, on the other hand, contain requirements that must be fulfilled by developers to make the resulting programming product HIPAA-compliant. Since the object of this article is providing a compliance list for software, it will focus on the Technical Safeguards and exclude the Physical and Administrative Safeguards from the following description.
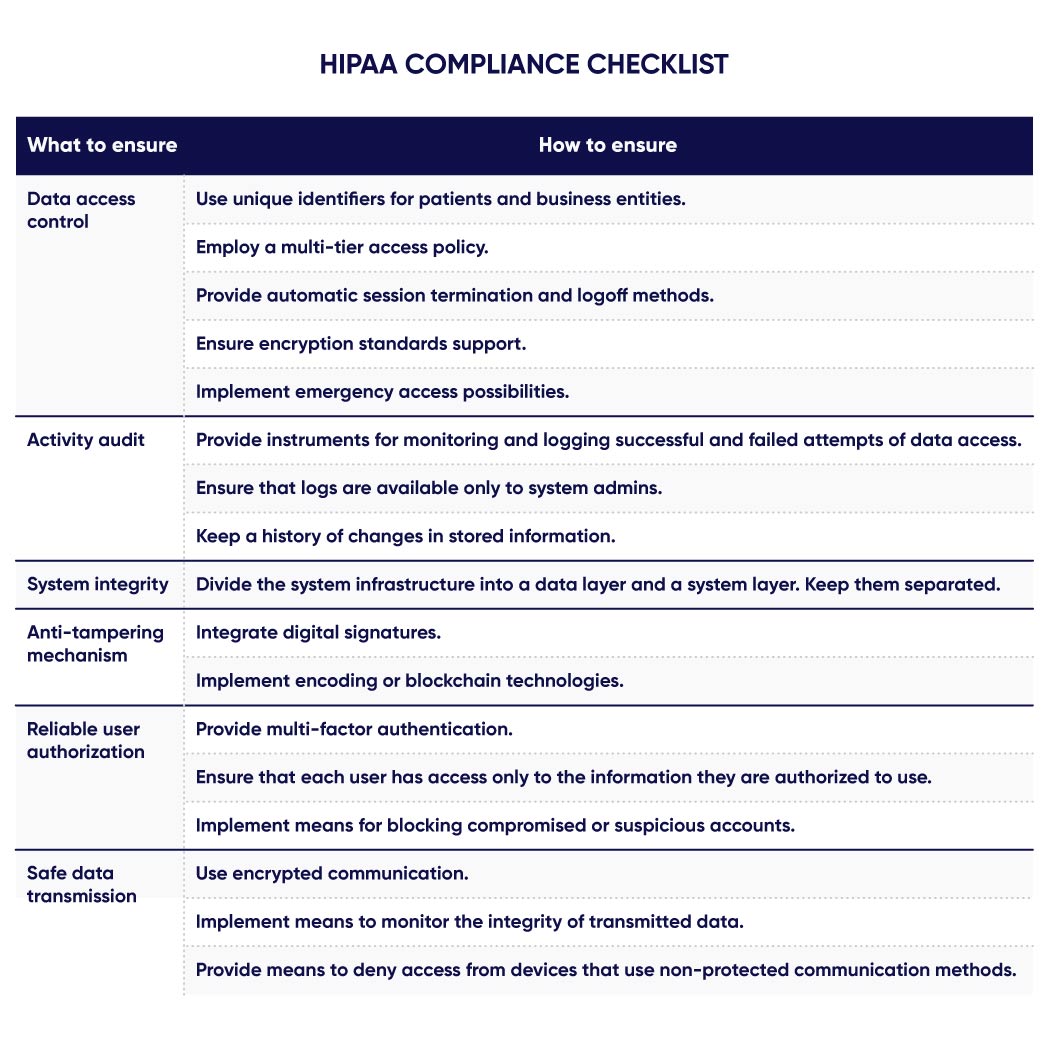
This compliance list contains six aspects covered by the Technical Safeguards.
- Data access control. Controlled access to ePHI can be ensured by a traditional “login+password” combination, as well as several additional ways.
- Using unique identifiers for patients and business entities.
- Employing a multi-tier access policy.
- Providing automatic session termination and logoff methods.
- Ensuring encryption standards support.
- Implementing emergency access possibilities.
- Activity audit. Access to ePHI must be monitored and logged. All events of changing, deleting, or simply viewing data must be recorded and stored, including their respective timestamps and user identifiers.
- Providing instruments for monitoring and logging successful and failed attempts of data access.
- Ensuring that logs are available only to system admins.
- Keeping a history of changes in stored information.
- System integrity. The optimal way of ensuring the integrity of a protected system is to establish its multi-layered structure with separately controlled access to each layer.
- Dividing the system infrastructure into a data layer and a system layer. Keep them separated.
- Anti-tampering mechanism. Providing mechanisms to detect tampering with data, identify all users who accessed it, and revert it to the original “uncorrupted” state with minimal or zero losses is crucial for secure systems.
- Integrating digital signatures.
- Implementing encoding or blockchain technologies.
- Reliable user authorization. The multi-tiered access structure must cooperate with multi-factor authentication. It must use all modern biometric methods that are made possible by smart devices: fingerprints, face scans, voiceprints, etc.
- Providing multi-factor authentication.
- Ensuring that each user has access only to the information they are authorized to use.
- Implementing means for blocking compromised or suspicious accounts.
- Safe data transmission. Developers must ensure that information cannot be intercepted during its transmission or at least cannot be decrypted or secretly altered by hackers.
- Using encrypted communication and modern protocols.
- Implementing means to monitor the integrity of transmitted data.
- Providing means to deny access from devices that use non-protected communication methods.
Conclusion
The long list of requirements that are regularly amended and added, as well as significant fines, only accentuate the importance of medical data protection. Keep in mind that currently there is no official HIPAA compliance certificate or other legal documents of approval issued by HSS or any other government authority for software products.
If you are determined to make your software application HIPAA compliant, use this checklist as a base and ensure the discussed requirements. Alternatively, contact us, and our specialists will help you with your task and offer several options. From the careful examination of your idea and providing comprehensive consults to full-scale software development when you get a custom-built HIPAA-compliant application according to your specification – select what option suits you best.



